(MENAFN- Frost & Sullivan)
The Elusive Promise of (and Maddening Obstacles to Implementing) a Cloud Zero Trust Architecture
A Zero Trust Architecture sets up organizations to scale for growth, allowing IT leaders to align security policy with business priorities.

This blog is excerpted from the Frost & Sullivan report, Insights for CISOs: How a Hybrid Island Strategy Accelerates Enterprise Cloud Zero Trust Architecture Transformation
Work today is cloud-first, device-agnostic, and remote. It's hard to envision a scenario dictating a return to the 1980s-like office, yet too many enterprises continue to try to protect employee work with“castle-and-moat” perimeter security first developed decades ago.
Contrast that approach with a cloud Zero Trust Architecture (ZTA) environment. In a cloud ZTA, connection and security are delivered at the cloud edge. A user connects directly to a resource. There is no network persistence and—with the internet serving as the connectivity backbone—considerably less infrastructure:
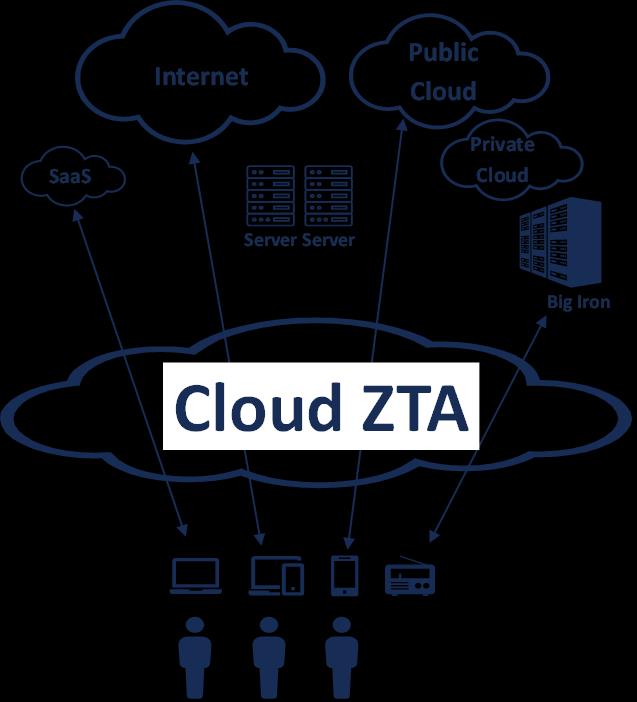
Figure 1. A Zero Trust Architecture providing converged connectivity and security as a cloud-edge service.
In a cloud ZTA environment, users enjoy an improved user experience. They can work anywhere, use devices most appropriate for their work, and work in the cloud (or on the internet, in the data center, or wherever they need to):
- Connectivity is direct , with security served from the (ideally, nearby) cloud edge.
- Routing can be optimized , minimizing hops between source device and destination, which optimizes performance.
- User experience is better because connectivity is consistent. Users in distant branch offices enjoy the same accelerated connectivity experience as C-suite users in headquarters.
A cloud Zero Trust Architecture protects the new way of work better than legacy castle-and-moat security:
- Security scales: Cloud-based ZTA solutions can scale to inspect much higher volumes of data traffic than bandwidth-constrained legacy hardware security appliances. Many can provide enough processing power and bandwidth to inspect encrypted data.
- Fixes are deployed instantly to every cloud edge : In a ZTA, fixes or updates can be deployed dynamically, securing every user within seconds. Contrast that with traditional hardware patching, which must be applied manually to every security gateway instance in every branch office.
- Threat actors cannot target what they cannot see: The ZTA obscures public IP address visibility behind its cloud-edge shield, further reducing the attackable surface.
- In a cloud ZTA environment, the proxy is both reverse and forward: Nothing bad gets in, nothing bad goes out .
- Blast radius is minimized : With no network persistence, cloud ZTA eliminates post-breach“east-west” lateral-movement threat risk.
The maddening impracticality of going all-in on cloud transformation There's an old security maxim that, paraphrased, applies here:“The best time to adopt a Zero Trust Architecture? Yesterday. But today is better than tomorrow.”
A ZTA offers a compelling proposition for IT security leaders: Dump networking infrastructure and outsource connectivity and security to a cloud Zero Trust Architecture solution provider. (The savings! The performance improvement! The corporate risk reduction!) And in theory, it's the perfect ideal for a greenfield deployment for, say, a multi-billion-dollar startup.
Such a transition goes by many names in cybersecurity marketing-speak: cloud transformation, digital transformation, security transformation. Marketing is easy. Enterprise IT transformation is hard. Whatever you call it, the wholescale enterprise leap to the cloud isn't trivial. And that's the problem: There's no such thing as a“greenfield” rollout for a major enterprise.
Though daunting, cloud transformation can be comparatively straightforward for organizations that rely exclusively on devices, assets, and resources that are already“cloud-enabled.” (Think laptops, smartphones, Chromebooks, etc. Point them at the cloud edge ZTA service, and you're good to go.) But what do you do when only“most” of your enterprise's systems are cloud-ready? What about that AS/400 that still houses mission-critical custom corporate applications? The ERP system that prints to a label maker? The IoT devices linked to hard-coded IP address destinations? The 10-year-old photocopiers designed for flat network-dependent sharing?
The measure of a technology's maturity is how well it enables an adopting organization to move forward. A Zero Trust Architecture sets up an organization to scale for secure business growth, allowing enterprise IT leaders to align security policy with business priorities. But a ZTA can deliver on its lofty promise only if an organization enters into transformation without the baggage of“cloud-unfriendly” legacy systems. Putting most but not all systems behind a cloud edge-served ZTA cybersecurity solution may improve an organization's security, but it isn't enough: It leaves the enterprise vulnerable, which sort of defeats the purpose of the ZTA rollout.
Cloud ZTA is an elegant, comforting, and aspirational ideal. But no existing enterprise is evergreen. A ZTA represents a huge leap—of faith, of technological advancement, of process redesign—for an organization that must maintain operations with vulnerable legacy infrastructure-dependent workflows.
Read more: Insights for CISOs: How a Hybrid Island Strategy Accelerates Enterprise Cloud Zero Trust Architecture Transformation
About Toph Whitmore

Senior cloud security analyst with twenty-plus years of tech experience in both the U.S. and Canada, including research, management consulting, executive leadership, and communications. Expertise in: Communications and messaging strategy, Business strategy, Digital transformation, Marketing operations management, and Project leadership.
View all posts by Toph Whitmore
MENAFN19092022005545012248ID1104890714
Legal Disclaimer:
MENAFN provides the information “as is” without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the provider above.