(MENAFN- PR Newswire)
Info-Tech Research Group's new blueprint provides insights for implementing a zero trust security model in the face of expanding attack surfaces and evolving cyberthreats. This comprehensive guide offers security leaders practical strategies to secure identities, data, and applications within perimeterless and hybrid environments. By addressing key challenges such as legacy mindsets, cloud integration, and data silos, the firm's insights show how organizations can enhance their security posture to navigate the complexities of modern digital landscapes more effectively.
TORONTO, Sept. 11, 2024 /PRNewswire/ - As organizations adapt to the complexities of hybrid work environments, they are increasingly challenged by the expanding attack surfaces created by a
perimeterless network. The breakdown of traditional network boundaries has made securing sensitive data and applications against evolving cyberthreats more difficult than ever. In response to this pressing issue, Info-Tech Research Group has introduced its latest blueprint, Secure Your Perimeterless Network , which highlights the importance of adopting a zero trust security model. This comprehensive resource offers essential guidance for security leaders and organizations aiming to protect identities, data, and applications, thereby strengthening their security posture in today's decentralized digital landscape.
Continue Reading
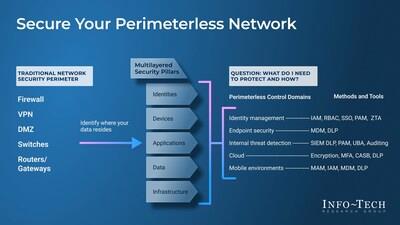
Info-Tech Research Group's "Secure Your Perimeterless Network" blueprint highlights key control areas security leaders and organizations should focus on when mapping a high-level zero trust architecture. (CNW Group/Info-Tech Research Group)
"Rather than thinking about securing the perimeter of your network, security leaders should think in terms of identities, data, and applications and where they reside and how you can protect them from threats no matter where they are located," says John Donovan , principal research director at Info-Tech Research Group . "Following the concept of data and information as the core of your security requirements, it is essential for strong end-to-end encryption to play a key role."
Info-Tech's data-backed resource highlights various challenges organizations face when transitioning to a zero trust security model in a perimeterless network environment. The firm reports that one of the most significant obstacles is the long-standing legacy mindset, which often hampers the adoption of innovative security approaches. The integration of cloud and SaaS environments adds further complexity, and a lack of familiarity with emerging technologies complicates the process even more. The blueprint further explains organizations must navigate cultural resistance and the challenges posed by complex systems and data silos, which limit interoperability. As cyberthreats continue to evolve, these challenges underscore the urgent need for strategic guidance to strengthen security frameworks in an increasingly dynamic digital landscape.
"With the increased attack surface of perimeterless networks – whether it is location, devices, or distributed resources in a cloud environment – security concerns are heightened," explains Donovan . "To address these risks, organizations must focus on identity, data, and applications in terms of end-to-end encryption, data loss prevention, and identity and access control."
The firm advises that zero trust is not a single product but a combination of multiple capabilities and that security leaders must understand the high-level architecture of zero trust to implement it effectively.
In its blueprint, Secure Your Perimeterless Network , Info-Tech recommends that security leaders and organizations should focus on the following key control areas when mapping out the architecture:
Identities: Users require identities with defined roles, access privileges, and controls such as multifactor authentication and single sign-on.
Devices: Devices also require endpoint protection and detection and defined access privileges.
Applications: Applications must be segmented by workflow, and administrative access must be limited.
Infrastructure: The infrastructure should be set up with monitoring and alerts.
Network: The internal network should not be treated as an implicit trust zone.
Data: Data must be encrypted in transit and at rest with allowlisted policies on how that data can be accessed and used.
Info-Tech's research findings will equip security leaders with the insights needed to effectively adopt a zero trust security model, which is crucial for securing perimeterless networks. By leveraging the firm's guidance, organizations can navigate the complexities of this transition, overcoming challenges such as interoperability issues and evolving threats. This strategic guidance not only enhances security posture but also ensures robust protection of identities, data, and applications.
For exclusive and timely commentary from John Donovan, an expert in infrastructure and operations, and access to the complete Secure Your Perimeterless Network
blueprint, please contact [email protected] .
Info-Tech LIVE 2024 Conference
Registration is now open for Info-Tech Research Group's annual IT conference, Info-Tech LIVE 2024 , taking place September 17 to 19, 2024, at the iconic Bellagio in Las Vegas . This premier event offers journalists, podcasters, and media influencers access to exclusive content, the latest IT research and trends, and the opportunity to interview industry experts, analysts, and speakers. To apply for media passes to attend the event or gain access to research and expert insights on trending topics, please contact [email protected] .
About Info-Tech Research Group
Info-Tech Research Group is one of the world's leading research and advisory firms, proudly serving over 30,000 IT and HR professionals. The company produces unbiased, highly relevant research and provides advisory services to help leaders make strategic, timely, and well-informed decisions. For nearly 30 years, Info-Tech has partnered closely with teams to provide them with everything they need, from actionable tools to analyst guidance, ensuring they deliver measurable results for their organizations.
To learn more about Info-Tech's divisions, visit McLean & Company
for HR research and advisory services
and
SoftwareReviews for software buying insights.
Media professionals can register for unrestricted access to research across IT, HR, and software and hundreds of industry analysts through the firm's Media Insiders program. To gain access, contact [email protected] .
For information about Info-Tech Research Group or to access the latest research, visit infotech
and connect via LinkedIn
and X .
SOURCE Info-Tech Research Group
WANT YOUR COMPANY'S NEWS FEATURED ON PRNEWSWIRE?
440k+
Newsrooms &
Influencers
9k+
Digital Media
Outlets
270k+
Journalists
Opted In
GET STARTED
MENAFN11092024003732001241ID1108663864
Legal Disclaimer:
MENAFN provides the information “as is” without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the provider above.