(MENAFN- AsiaNet News) Amid the ongoing Lok Sabha elections, cyber threats against Indian government, military entities and aerospace sectors have escalated, with notable attacks traced back to Pakistan-based threat groups.
A recent report by the Blackberry Research & Intelligence Team has revealed that Transparent Tribe, also known as APT36, has been actively targeting Indian institutions with sophisticated cyber espionage tactics. This group, operational since 2013, has previously focused on India's education and defence sectors, using advanced methods and tools to infiltrate and extract sensitive information.
Transparent Tribe, also referred to by aliases such as ProjectM, Mythic Leopard, and Earth Karkaddan, continues to adapt and refine its attack strategies. The group's recent activities, spanning from late 2023 to April 2024, demonstrate a shift towards leveraging modern programming languages like Python, Golang, and Rust. They are also exploiting popular web services, including Telegram, Discord, Slack, and Google Drive, to facilitate their malicious operations.
"We observed the group deploying a range of malicious tools mirroring those used in previous campaigns as well as newer iterations, which we assess with moderate to high confidence were indeed conducted by Transparent Tribe," the report stated.
"Throughout our investigations, we uncovered multiple artifacts that substantiate our attribution. For example, we noted that a file served from the group's infrastructure set the time zone (TZ) variable to“Asia/Karachi," which is Pakistani Standard Time. We also discovered a remote IP address associated with a Pakistani-based mobile data network operator embedded within a spear-phishing email. The strategic targeting of critical sectors vital to India's national security additionally suggests the group's potential alignment with Pakistan's interests," it further noted.
Also read:
BEWARE of the 'Joker' scam: How cybercriminals are exploiting innocent housewives, job-seekers in India
Methods and Tactics of Transparent Tribe
Among the more alarming discoveries is Transparent Tribe's use of an "all-in-one" espionage tool written in Golang. This tool, capable of cross-platform functionality, was distributed via domains mimicking legitimate Indian entities. The downloader retrieves and executes final payloads, including modified versions of open-source projects like Discord-C2, for data exfiltration. Additionally, in October 2023, Transparent Tribe incorporated ISO images as an attack vector, highlighting their evolving tactics.
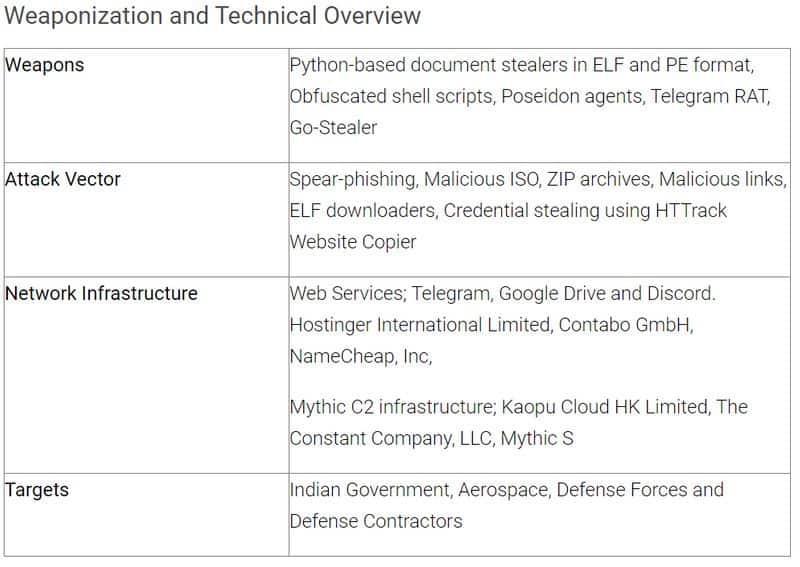
The group also uses customized versions of open-source projects like Discord-C2 and Slack for their C2 operations. These tools are modified to include capabilities similar to their previous malware, such as GLOBSHELL and PYSHELLFOX, which are used for file exfiltration and browser session hijacking.
Transparent Tribe's arsenal includes various ELF binaries, Python scripts, and Windows executables designed to exfiltrate sensitive information. These tools monitor directories for files with specific extensions, such as .pdf, .docx, .xlsx, and .jpg, and send them to the attackers' servers.
Exploitation of Popular Web Services
Phishing remains the primary method of delivering malicious payloads for Transparent Tribe. The group typically employs spear-phishing emails containing malicious ZIP archives or links.
"India has put significant efforts into the research and development of indigenized Linux-based operating systems such as MayaOS. MayaOS - developed internally by the Indian Defence Research and Development Organisation (DRDO), the Centre for Development of Advanced Computing (C-DAC), and the National Informatics Centre (NIC) - serves as an alternative to Windows. It is a hardened Linux distribution intended for adoption by the Indian Ministry of Defence (MoD) and subsequently the country's Army, their Navy and their Airforce," the report stated.
"As a result, Transparent Tribe has chosen to focus heavily on the distribution of Executable and Linkable Format (ELF) binaries during this period," it noted.

Evidence of Pakistani Origin and Strategic Alignment
The hackers have also utilized popular messaging apps for command-and-control (C2) and data exfiltration purposes. Tools like a Python-based Telegram bot compiled into a Windows executable were used to target Indian Defence Forces. The group also used Slack for data exfiltration, reflecting their strategy of leveraging widely-used platforms to remain undetected.
BlackBerry's analysis confirms with moderate to high confidence that Transparent Tribe's operations are aligned with Pakistani interests. This attribution is supported by operational security mistakes, such as setting the time zone to Pakistani Standard Time and the use of a Pakistani IP address in their infrastructure.
The group's persistent targeting of India's defence sector underscores a clear strategic alignment with Pakistan's geopolitical goals. BlackBerry has included a comprehensive list of indicators of compromise (IoCs) to aid in detection and mitigation efforts.
BlackBerry's report concludes that Transparent Tribe's activities are part of a broader, persistent effort to infiltrate and exfiltrate sensitive information from India's critical sectors. The group's evolving tactics, use of cross-platform programming languages, and exploitation of popular web services indicate a high level of adaptability and sophistication.
"This activity is expected to continue," the report warns, highlighting the ongoing threat posed by Transparent Tribe amid escalating geopolitical tensions.
MENAFN01062024007385015968ID1108283408
Legal Disclaimer:
MENAFN provides the information “as is” without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the provider above.