
Hybridpetya Ransomware Breaks Secure Boot Barrier On UEFI Systems - Arabian Post
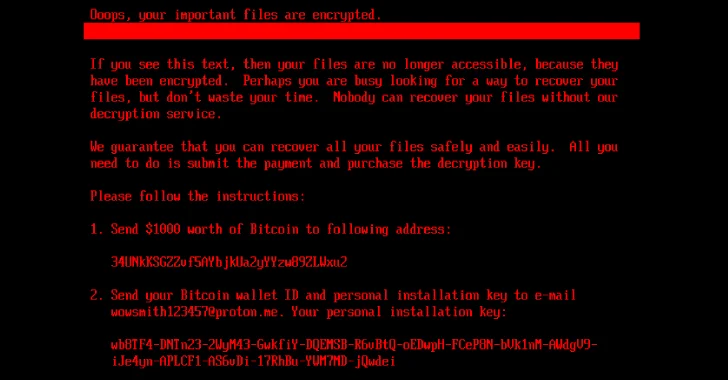
Security researchers at ESET have identified a new malware strain called HybridPetya that combines traits of Petya and NotPetya ransomware with advanced boot-kit functionality to infect systems protected by UEFI Secure Boot. It exploits the vulnerability CVE-2024-7344 in the Howyar“Reloader” UEFI application to bypass signature checks, allowing unverified code execution.
HybridPetya was first spotted when samples uploaded to VirusTotal in February 2025 caught the eye of ESET's threat analysts. The malware installs a malicious EFI application into the EFI System Partition, which then encrypts the Master File Table on NTFS-formatted drives. The MFT contains metadata about all files, making its encryption especially disruptive.
One variant of HybridPetya takes advantage of CVE-2024-7344 to dodge the Secure Boot mechanism. The exploit leverages a file named cloak. dat, which carries an XOR-encoded bootkit. When the vulnerable reloader. efi is executed at boot, it checks for cloak. dat on the EFI System Partition and loads its content without validating integrity, thus undermining UEFI Secure Boot protections. Systems with Microsoft's January 2025 dbx update are said to be protected against this exploit.
HybridPetya also includes features for standard installer-based deployment. It determines whether the system uses UEFI with GUID Partition Table layout, locates the EFI System Partition, replaces or backs up legitimate bootloaders, and drops configuration, key material, and progress-tracking files into the EFI partition. A blue screen of death is triggered to force a reboot and activate the bootkit. Decryption is possible: victims supply a 32-character key, which if correct restores bootloaders and decrypts encrypted clusters.
ESET reports no evidence that HybridPetya has been used in large-scale attacks so far; there is concern that it might be a proof-of-concept or under limited testing. Analysts warn that its technical capabilities-especially Secure Boot bypass, bootkit deployment, and MFT encryption-represent a formidable escalation in ransomware threat design.
See also UAE and Samsung partner for new innovation campusCVE-2024-7344 was disclosed in January 2025. It relates to the Howyar UEFI Application“Reloader” which permits execution of unsigned software from a hardcoded path. The vulnerability has high severity, given its impact on integrity and confidentiality.
Organisations running Windows systems with UEFI Secure Boot are urged to verify that the January 2025“dbx” revocation list update has been applied. Systems lacking this update remain vulnerable. Security teams are also advised to monitor for indicators such as unexpected files in EFI partitions, anomalous versions of bootloader backups, or unexpected“counter” files tracking encryption status.
Notice an issue? Arabian Post strives to deliver the most accurate and reliable information to its readers. If you believe you have identified an error or inconsistency in this article, please don't hesitate to contact our editorial team at editor[at]thearabianpost[dot]com . We are committed to promptly addressing any concerns and ensuring the highest level of journalistic integrity. Legal Disclaimer:
MENAFN provides the
information “as is” without warranty of any kind. We do not accept
any responsibility or liability for the accuracy, content, images,
videos, licenses, completeness, legality, or reliability of the information
contained in this article. If you have any complaints or copyright
issues related to this article, kindly contact the provider above.
Most popular stories
Market Reseach
- B2PRIME Strengthens Institutional Team's Growth With Appointment Of Lee Shmuel Goldfarb, Formerly Of Edgewater Markets
- BTCC Exchange Scores Big In TOKEN2049 With Interactive Basketball Booth And Viral Mascot Nakamon
- Ares Joins The Borderless.Xyz Network, Expanding Stablecoin Coverage Across South And Central America
- Primexbt Launches Stock Trading On Metatrader 5
- Solana's First Meta DEX Aggregator Titan Soft-Launches Platform
- Moonacy Protocol Will Sponsor And Participate In Blockchain Life 2025 In Dubai
- Primexbt Launches Instant Crypto-To-USD Exchange



















Comments
No comment